Windows 10 Ransomware Discovered
Christopher Files / 9 years ago

Well this didn’t take long! A new form of ransomware has been discovered which if downloaded, will automatically encrypt your files before demanding a fee to unlock them. The distributors of this malicious code are attempting to impersonate Microsoft by “offering” users a free upgrade via email. This scam takes full advantage of the Windows 10 download process, which asks consumers to virtually wait in a metaphorical line for the upgrade.
So how does it work?
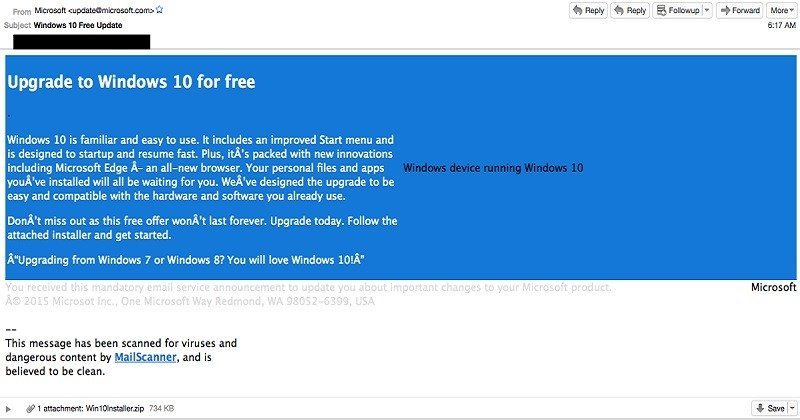
The distribution works by sending an email to consumers offering them a free Windows 10 upgrade. A sample of this type of email is below, firstly, the “from” address on the email is spoofed, (update<at>microsoft.com). This is not actually from Microsoft but from an IP address in Thailand. The attackers are also using a similar colour scheme to that of Microsoft with the aim of luring consumers into associating this email as genuine.
The next red flag is courtesy of the letter format which does not parse properly. This could be due to the targeted audience, a demographic using a non-standard character set, or the character set the adversaries were using to craft the email. Another suspicious but sneaky technique is the mail virus scanner which indicates the email is fine, it links to an open source mail scanner, but this is designed to trick users.
What is the Payload of the virus?
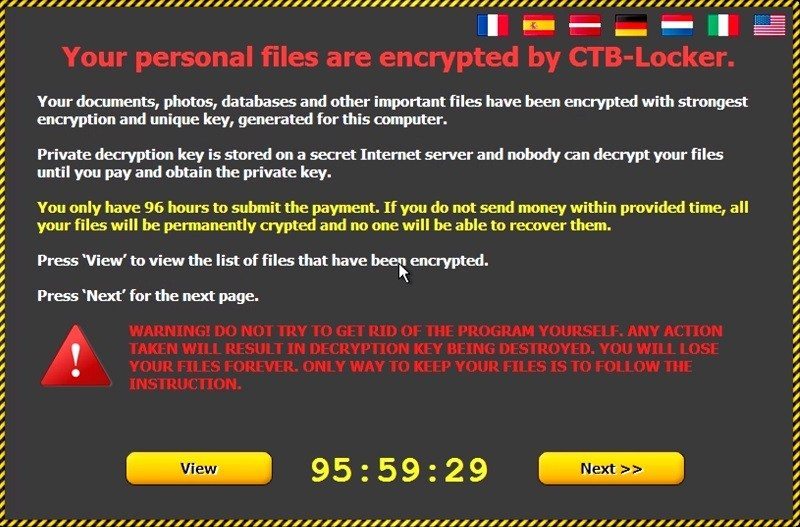
If this email is taken as a genuine correspondent from Microsoft, you will be asked to download a zip file which contains an executable file. Once run, the below screenshot will pop up. The payload is CTB-Locker, a ransomware variant and is currently being delivered to users at a high rate, whether it is via spam messages or exploit kits, adversaries are dropping a huge amount of different variants of ransomware. The functionality is similar to this kind of ransomware with a few extra features which include, the use of elliptical curve encryption which provides the same public/private key encryption but it’s a different type of algorithm with lower overheads.
Another feature for this locker includes using hard-coded IP addresses on non-standard ports to establish communication. There is also a significant amount of data being exchanged between systems, which are largely uncharacteristic for ransomware. An analysis of network traffic reveals that there were ~100 network streams to various IP addresses. The most common ports being utilized are 9001, 443, 1443, and 666.
So how do I protect myself from this threat?
Be very careful with emails of this nature, look at the details and if unsure, research it, this is a powerful weapon at staying current and educated on the nature of these threats. Always question a “Free Upgrade” which is sent to your inbox, never open or install executable or any other file without checking the authenticity of the email and file. If in doubt, don’t open it.
These scams are becoming more sophisticated for the average user with the aim of virtually locking your files up. Always perform regular backups and use an up to date antivirus scanner as a matter of course.
Thank You to Cisco Blogs for providing us with this information
Image courtesy of digitallife



















