GCHQ-Developed Encryption System Has Built-In Backdoor
Ashley Allen / 9 years ago
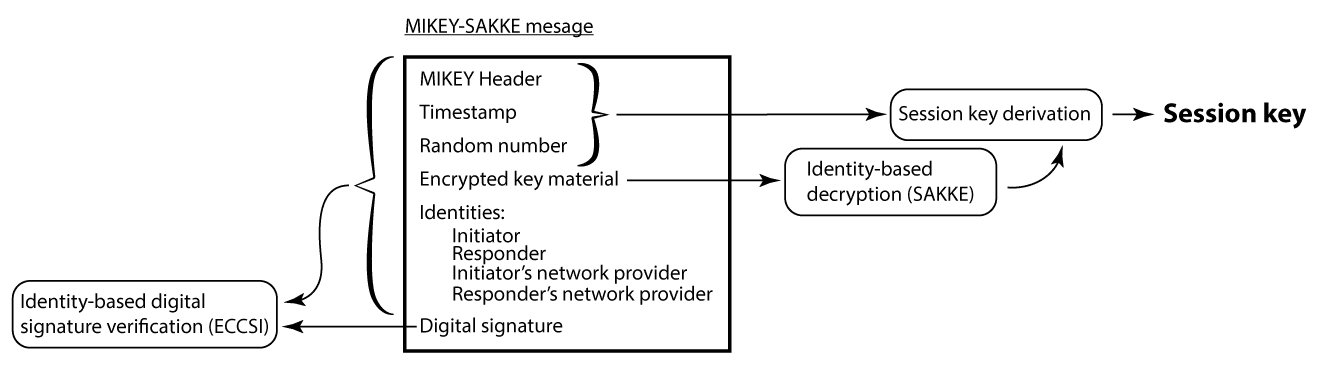
A security researcher has discovered that a telephone encryption system developed by UK intelligence agency GCHQ contains a backdoor that can be exploited by anyone who has its master key. Steven J. Murdoch, a Royal Society University Research Fellow in the Information Security Research Group of University College, found that the MIKEY-SAKKE protocol, based on the Secure Chorus encryption standard, can be bypassed using the private master key to decrypt and collect call data in bulk.
“The existence of a master private key that can decrypt all calls past and present without detection, on a computer permanently available, creates a huge security risk,” writes Murdoch, “and an irresistible target for attackers. Also calls which cross different network providers (e.g. between different companies) would be decrypted at a gateway computer, creating another location where calls could be eavesdropped.”
The existence of an encryption form that allows intelligence services to decrypt and access data comes as no surprise since the UK – in the form of both Prime Minister David Cameron and MI5 Director-General Andrew Parker – have declared war on end-to-end encryption as it prevents their mass surveillance efforts.
“GCHQ designs the encryption technology used by government to prevent unauthorised parties having access to classified information,” Murdoch added. “But GCHQ also wants the ability to examine how this encryption technology is used to investigate suspected leaks whether to companies, the press, or foreign intelligence agencies.”



















