New Windows Ransomware Paralyses Companies Across Europe
Ashley Allen / 7 years ago
A new ransomware – with a familiar history – is sweeping across Europe, infecting banks, businesses, and airlines. The malicious program, known as Petya/Petwrap, swept across Ukraine this morning. However, within hours, the software had spread into Europe. So far, victims include the Ukrainian government, Kiev’s Boryspil Airport, Danish shipping company Maersk, and Russian oil giant Rosnoft. Reports suggest bodies in India, Spain, France, the UK have also been infected. A global contamination is now occurring:
Petrwrap/Petya ransomware variant with contact wowsmith123456@posteo.net spreading worldwide, large number of countries affected.
— Costin Raiu (@craiu) June 27, 2017
So, what’s so familiar about Petya/Petwrap? The ransomware uses EternalBlue – the basis of the WannaCry malware that hit Windows systems in May – to proliferate itself.
What is EternalBlue?
The US National Security Agency (NSA) developed the EternalBlue Windows exploit. It uses a vulnerability in Microsoft’s Server Message Block (SMB) protocol to execute code on a target computer. The exploit was leaked – along with a number of other hacking tools – by Shadow Brokers in April 2017. It is a key constituent of the WannaCry malware. Following the WannaCry attack, Microsoft issued emergency patches for Windows 7, Windows 8, Windows XP, and Windows Server 2003.
Petya/Petwrap
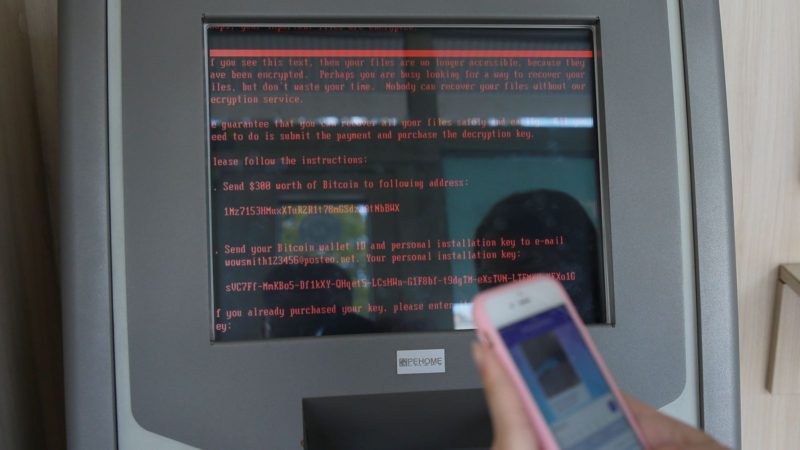
Petya is a year old, but its marriage with EternalBlue makes it more dangerous than ever. The malware’s accelerated infection rate certainly mirrors that of WannaCry. Systems infected with Petya/Petwrap bear the following message (via Quartz):
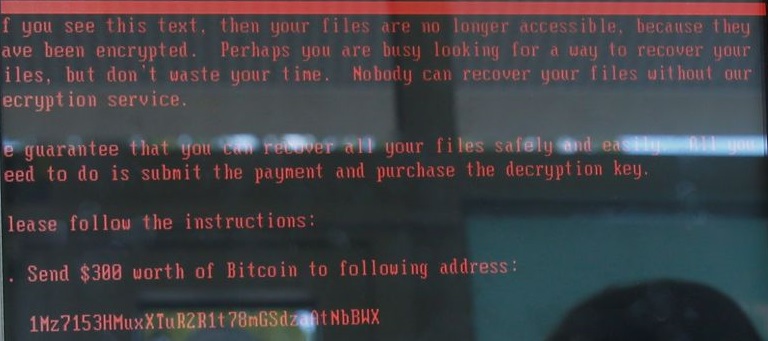
The ransomware demands $300 in Bitcoin. Funnily enough, that is the same ransom WannaCry asks for. Is this an attack by the same parties? Shadow Brokers did warn of more developments in June. Is Petya/Petwrap one of them?



















