Researchers Find Malware Hiding in GIFs
Ashley Allen / 8 years ago

Security researchers have found a type of malware on popular websites which hides in advertisement images and has been active for around two years. The Stegano exploit kit – discovered by Eset researchers – finds vulnerable computers and displays a custom GIF, the alpha channel of which contains malicious code. That code can then redirect the browser to a malicious site. The good news is that, for most readers, you’re probably safe: the exploit requires both Internet Explorer and Flash in order to work, and you’ve likely abandoned that disastrous pair by now (if you haven’t yet, do so immediately).
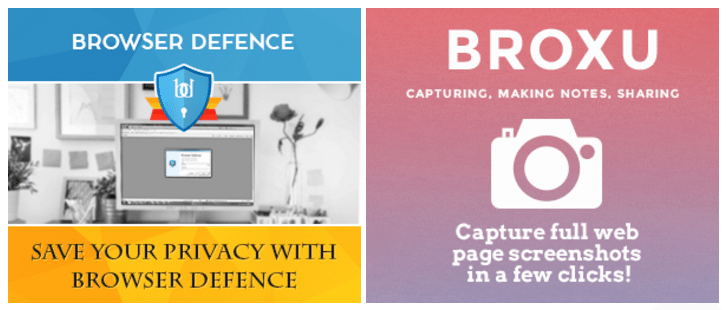
“Millions of readers who visited popular news websites have been targeted by a series of malicious ads redirecting to an exploit kit exploiting several Flash vulnerabilities. Since at least the beginning of October, users might have encountered ads promoting applications calling themselves “Browser Defence” and “Broxu” using banners similar to the ones below:
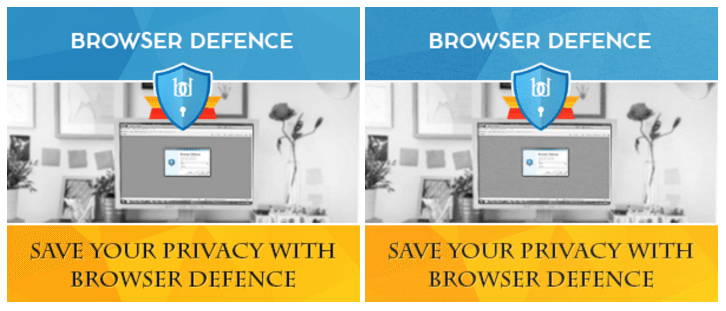
Without requiring any user interaction, the initial script reports information about the victim’s machine to the attacker’s remote server. Based on server-side logic, the target is then served either a clean image or its almost imperceptibly modified malicious evil twin.
The malicious version of the graphic has a script encoded in its alpha channel, which defines the transparency of each pixel. Since the modification is minor, the final picture’s color tone is only slightly different to that of the clean version:
Using the known Internet Explorer vulnerability CVE-2016-0162, the encoded script attempts to verify that it is not being run in a monitored environment such as a malware analyst’s machine.
If the script does not detect any signs of monitoring, it redirects to the Stegano exploit kit’s landing page, via the TinyURL service. The landing page loads a Flash file that is able to exploit three different vulnerabilities (CVE-2015-8651, CVE-2016-1019, CVE-2016-4117), depending on the version of Flash found on the victim’s system.
Upon successful exploitation, the executed shell code collects information on installed security products and performs – as paranoid as the cybercriminals behind this attack – yet another check to verify that it is not being monitored. If results are favorable, it will attempt to download the encrypted payload from the same server again, disguised as a gif image.
The payload is then decrypted and launched via regsvr32.exe or rundll32.exe. Payloads detected so far include backdoors, banking trojans, spyware, file stealers and various trojan downloaders.”
The exploit remained secret for so long by hiding its malicious data within the alpha channel, which is a transparency layer, like so:
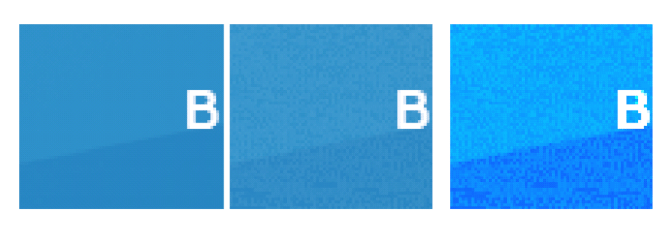
The third image above is an enhancement of the second, which shows the QR-like code hiding within the alpha channel. Should the target computer be running any security-enhancing software, though, an image without that dangerous transparency appears. Pretty sneaky.
As if you needed another lesson: don’t use Internet Explorer and don’t use Flash.
Image courtesy of EFF-Graphics.



















