WannaCry Analysis Points to China
Ashley Allen / 8 years ago
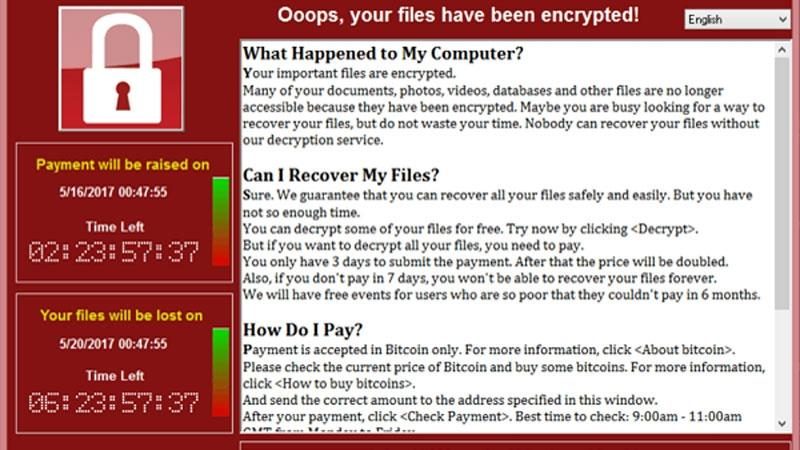
A new investigation suggests that WannaCry – the ransomware that, earlier this month, downed Windows systems globally – was made in China. Translation software was responsible for the creation of twenty-five WannaCry ransom notes. However, researchers determined that a person was responsible for writing two versions of the note: English and Chinese.
WannaCry – Written in Fluent Chinese
Cybersecurity group Flashpoint examined the languages used within every regional variation of the ransom note. Twenty-eight ransom notes, written in different languages, feature within the malware. Flashpoint found that twenty-five of the notes tallied with machine translations. Fluent speakers, though, were responsible for the other three: English, Chinese (Simplified), and Chinese (Traditional). However, only Chinese read as though written by native speakers.
Flashpoint reports:
“Analysis revealed that nearly all of the ransom notes were translated using Google Translate and that only three, the English version and the Chinese versions (Simplified and Traditional), are likely to have been written by a human instead of machine translated. Though the English note appears to be written by someone with a strong command of English, a glaring grammatical error in the note suggest the speaker is non-native or perhaps poorly educated.”
Chinese Text, Simplified and Traditional
When we refer to written ‘Chinese,’ we mean the globally recognised Traditional or Simplified character sets. Of course, when spoken, there is no singular Chinese language. Instead, there are up to 13 variations of the native language. These include Mandarin, Cantonese, Wu, Min, and Yue. Mandarin, spoken by 70% of Chinese speakers in China and Singapore, is the most popular variant.
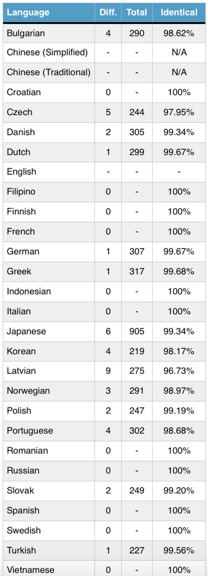
Ransom Note Variations – 96% Match Through Google Translate
The English variation, it seems, was the basis for the translation variations. The report explains:
“Flashpoint found that the English note was used as the source text for machine translation into the other languages. Comparisons between the Google translated versions of the English ransomware note to the corresponding WannaCry ransom note yielded nearly identical results, producing a 96% or above match.”
The following table shows the similarity between the different WannaCry ransom notes and the text as put through Google Translate:
WannaCry’s Chinese Influence
While the Flashpoint investigation points to Chinese natives as being responsible for WannaCry, there is no suggestion that the Chinese State is responsible for the ransomware. As Flashpoint concludes:
“Flashpoint assesses with high confidence that the author(s) of WannaCry’s ransomware notes are fluent in Chinese, as the language used is consistent with that of Southern China, Hong Kong, Taiwan, or Singapore. Flashpoint also assesses with high confidence that the author(s) are familiar with the English language, though not native. This alone is not enough to determine the nationality of the author(s).”
The author(s) of WannaCry have disappeared since the launch of the infection. Those responsible have shut down WannaCry’s control system and paid Bitcoin ransoms remain unclaimed. Cybersecurity expert Professor Alan Woodward told the BBC:
“I actually think they’ve run for the hills.
They know that so many people are watching them now and that following the money could lead to their downfall. I suspect if they’ve got any sense at all they’ll leave it well alone.”
WannaCry’s Legacy
While the WannaCry drama may be over, the ransomware’s big brother, dubbed EternalRocks, is already out in the wild. It uses seven NSA hacking tools, compared to the two used by WannaCry. Shadow Brokers, the team responsible for leaking the NSA hacking tools, has warned of more leaks next month.



















